In this post I will outline how to use zones to create public firewalled networks. A device that can bring up multiple interfaces per radio is very attractive here. One essid for private wireless and another for open public wireless. The Atheros ath9k chipsets are very well supported in this regard because they are free software.
This post is different than my older post where we have a private LAN behind our WAN interface that we need to protect… In this scenario we have our ISP connected directly to the openWRT WAN port and we need to bring up a public wireless that is segregated from the LAN. Like so:
"public wifi"
/
ISP <-openWRT fw-> LAN 192.168.1.0/24 <-public_zone-> PUBLIC 172.16.134.0/24
\
"private LAN wifi"
Obviously the zone can be utilized however you like. Another common option would be to firewall a open wireless network from the LAN. And forgo the insecure nature of a “secured” wireless altogether. The OpenWRT could be running openvpn, that you connect to over the “insecure” wireless, now thats secure!
The following steps are done via the web interface (luci).
1. Start by adding a new wireless interface. In this case to the 5ghz radio. You can do this again for the 2.4ghz radio. 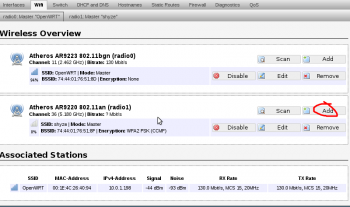
2. Set the essid and network name “public”. This will allow us to use firewall zones to segregate the networks, rather than excluding individual rfc1918 subnets like in the first example.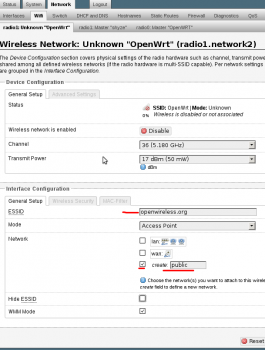
3. Edit the interface “PUBLIC” so that we can set it as a static ip.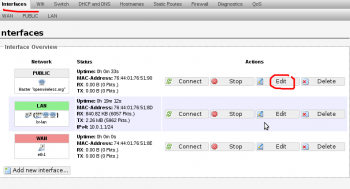
4. Change the protocol to “static address” set a ip for it and a subnet. DO NOT set a gateway. This will write a new default gateway to the routing table and cause the internet to break occasionally. Setup a dhcp server for this network.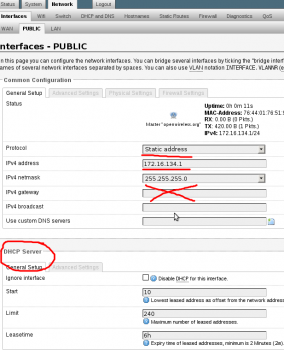
5. In the firewall section. Setup a zone called something like “public_zone” and assign it to the “public” network. And allow it to forward to “WAN” zone.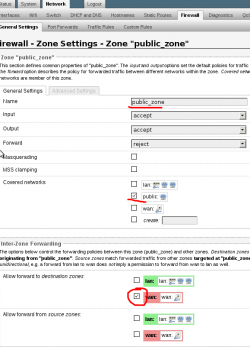
6. This is what the general firewall zone’s should look like now.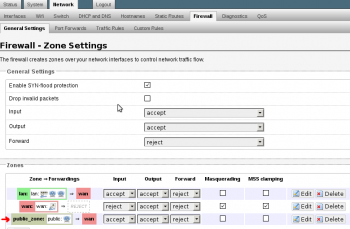
Be sure to test it. Connect to the public and try and nmap a known host on the private and vice versa. A few times I have needed to reboot the router for everything to start working properly. It could be because I tinkered too much and caused a hickup. Just something to keep in mind..
Leave a Reply