In this scenario we will be implementing a openWRT as a wireless access point only. One wireless essid will be LAN accessible and the other will be segregated from the LAN but able to access the WAN. The openWRT in this example will not be the gateway to the network. Another device is the gateway and there is an existing dhcp server.
PUBLIC wifi
172.16.134.0/24
|
public gateway and dhcp server
172.16.134.1
\
Source NAT to 10.101.101.10
\
ISP <-Gateway-> LAN wired 10.101.101.0/24 <-openWRT->
/
LAN wifi (wpa2+aes)
10.101.101.0/24
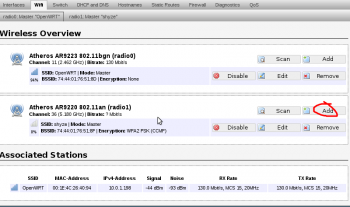
1. Add a new wireless access point
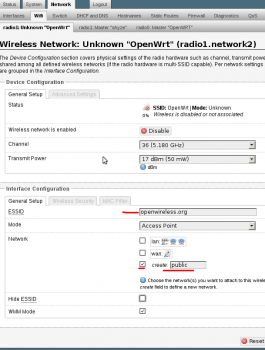
2. Settings for the new wireless access point. Create a new network interface of “public”. Don’t use any encryption, as this is for general public use.
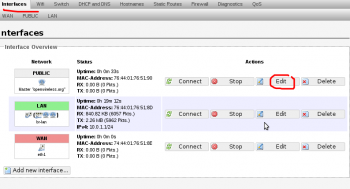
3. Edit network interface for the public network
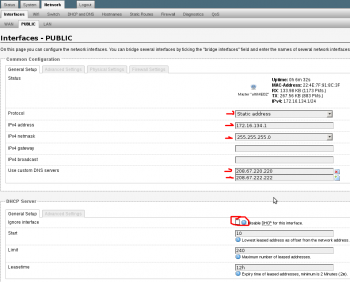
4. Edit PUBLIC interface settings. Set to static address and enable DHCP server for this new network.
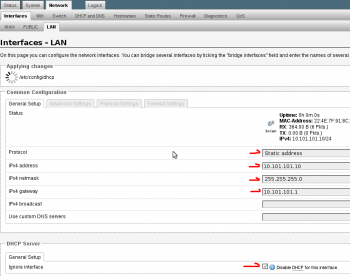
5. Edit the LAN interface. Set the lan interface to an un-used ip of the existing network. Don’t set to “dhcp client” as you will lose connectivity and need to perform a recovery on your openwrt device. Be sure to disabled the DHCP server as the existing network already has one.
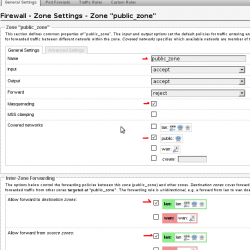
6. Add a new zone and call it “public_zone”. Masquarade it and put it in the public network. Allow forwarding to and from “lan” zone. We will limit this later with specific firewall rules.
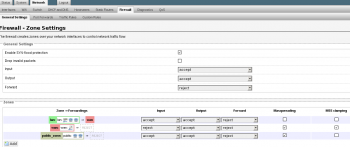
7. This is what the general firewall zones should look like
8. Under the Firewall -> Traffic Rules section add a new Source NAT Rule. Call it “pub2lan“. Set the “Source zone” to “public_zone” and the “Destination zone” to “lan” and set the drop down option “To source IP” to br-lan interface, in this example its 10.101.101.10. Leave “To source port” blank. This SNAT rule will translate all traffic on the public wireless network of 172.16.134.0/24 into the IP of 10.101.101.10. This is the redirect rule from /etc/config/firewall
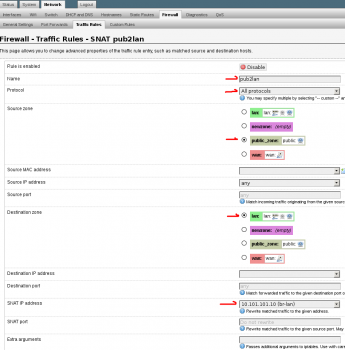
config redirect
option target 'SNAT'
option src 'public_zone'
option dest 'lan'
option proto 'all'
option name 'pub2lan'
option src_dip '10.101.101.10'
option enabled '1'
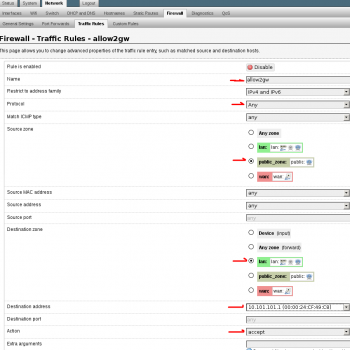
9. Setup a “New forward rule:” Set name to allow2gw or similar. Source zone to “public_zone” Destination zone to “lan” Click “Add and edit…” Protocols should be “Any”, Destination address is the gateway of the network. In this case 10.101.101.1. The following is the /etc/config/firewall rule for reference. This will allow traffic from the public_zone to reach the gateway of the network.
config rule
option target 'ACCEPT'
option proto 'all'
option name 'allow2gw'
option src 'public_zone'
option dest 'lan'
option dest_ip '10.101.101.1'
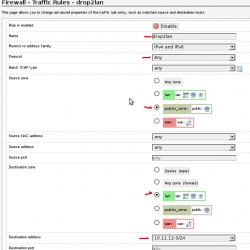
10. Setup a “New forward rule”. Set the name to drop2lan or similar. Set the Source zone to “public_zone” and Destination zone to “lan”. Click “Add and edit…” Set Protocol to “Any”, Destination address to custom and enter the subnet of the LAN. In this case its 10.101.101.0/24, set “Action” to “drop”. You can add more rules like this one to limit access to other networks or hosts as needed.
config rule
option name 'drop2lan'
option src 'public_zone'
option proto 'all'
option target 'DROP'
option dest 'lan'
option dest_ip '10.101.101.0/24'
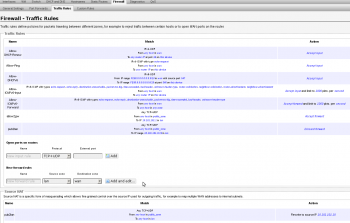
11. Firewall Traffic Rule overview. There is an error on this view. The following rules have “option proto ‘all’” set and the luci web interface shows “Any TCP+UDP”. This is simply a bug in the luci interface and can be ignored. The order of these rules is very important. In this case you can see we added the “Allow to 10.101.101.1” before the “Drop to 10.101.101.0/24”. If reversed, the lan including the gateway would not be accessible from the public wireless AP. Therefore, you would not be able to reach the Internet.
Leave a Reply